Edge Computing Has Risks that Can be Addressed with Computational Storage.
- Home / NGD Systems /
- Edge Computing Has Risks that Can be Addressed with Computational Storage.
Edge Computing Has Risks that Can be Addressed with Computational Storage.
A variety of edge computing implementations exist, and each requires careful alignment with networks services and infrastructure. I&O leaders responsible for networking will optimize performance and costs, and reduce risks, by following the guidance in this research.
The topology directive of edge computing is not new. However, the demands of the plethora of latency-sensitive devices at the remote locations are new. An edge computing approach is intended to reduce latency and minimize bandwidth demands by locating application intelligence, storage and compute closer to endpoints, rather than in a remote server or data center.
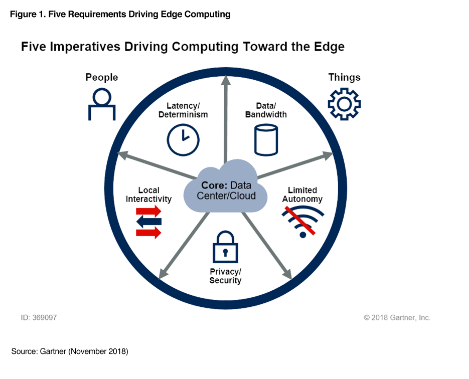
Edge computing represents an emerging topology-based computing model that enables and optimizes extreme decentralization. However, it is still synergistic with a centralized core, whether traditional data center or hyperscale cloud provider. It places intelligence, storage and other functionality close the edge, where people and endpoints, such as sensors or monitors in an IoT deployment, produce, analyze or consume information. Gartner has identified five requirements that drive edge computing.
Below you will see our take on their “Five Imperatives Driving Computing toward the Edge” today. Fill out the form to read their un-biased view on these issues and then just reach our for how we truly aid your deployments today!
Computational Storage Helps Address
Many Issues at the Edge
How can you effectively utilize edge computing and solve the challenges in data, diversity, protection, and locations? Read what Analysts are saying about the changing infrastructure:

Latency is imperative – Our Computational Storage products allow for this to be managed more effectively than any existing architecture, especially in edge constrained environments

Minimizing the attack surface by ensuring that edge computing hardware, software, applications, data, and networking have security and self-protection built-in.

Bandwidth is increasing, Still Clogged – With Computational Storage doing localized processing the amount of bandwidth needed for value from data is reduced significantly

Investing in technologies that automate data management and governance at the edge as much as possible.
GARTNER is a registered trademark and service mark of Gartner, Inc. and/or it’s affiliates in the U.S. and internationally, and is used herein with permission.
This graphic was published by Gartner, Inc. as part of a larger research document and should be evaluated in the context of the entire document. The Gartner document is available upon request from NGD Systems.
All rights reserved.
Gartner, Minimize the Network Risk of Edge Computing, By Analysts Danellie Young, Bill Menezes, Liza Pierce, 2 November 2018, ID G00369097
Jos Keulers administrator
About the author